This post will explore all the features in Faction that you can use to convert your report templates to Faction automated report templates and create boilerplate text that is easy to integrate into your reports. This will save you hours of time so you can spend more time hacking apps! This will also briefly touch on how to use Faction as an ASPM solution to track your findings to remediation.
A Great Pentest Needs a Great Report
Your pentest report is the key to building trust and credibility with your clients. It should be polished, consistent, aligned with your brand, and contain all the technical details your clients need to understand the risks behind each finding. With Faction, creating professional reports is simple, thanks to our customizable report templates.
Faction templates are in DOCX format, so you can easily build and update them using MS Word or LibreOffice — no fancy tools required.
If your team has been doing this for a while, you probably already have a report theme and layout you don’t want to change. It probably has a slew of highlighted items that need to be updated on every assessment. For example: client name, executive summary, risk assessment, etc. It might look something like this:
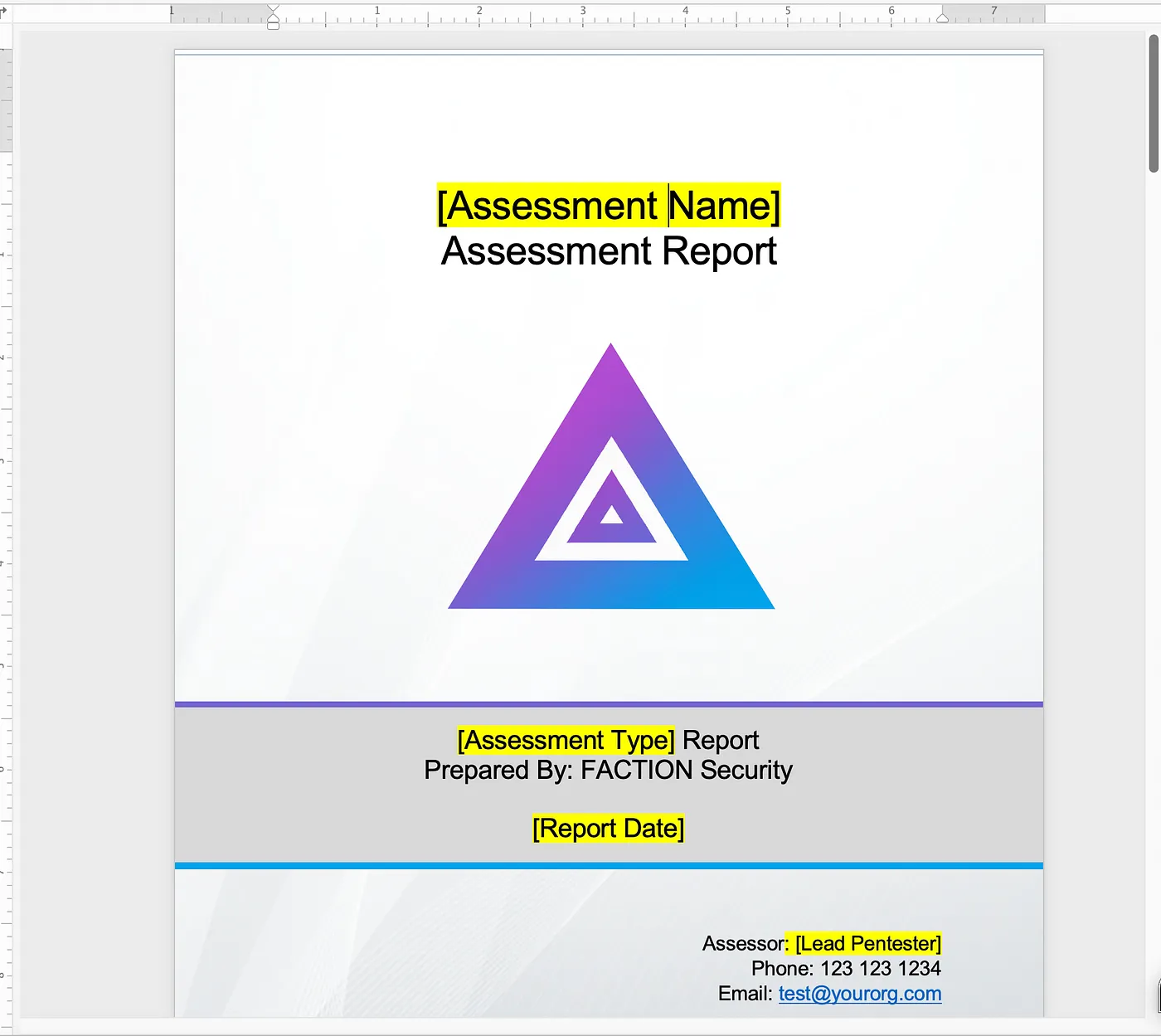
With Faction, you can take your existing report and replace all those highlighted elements with Faction’s variables, and you're done! No more match and replace as Faction will populate these fields for you. That template above now looks like this:
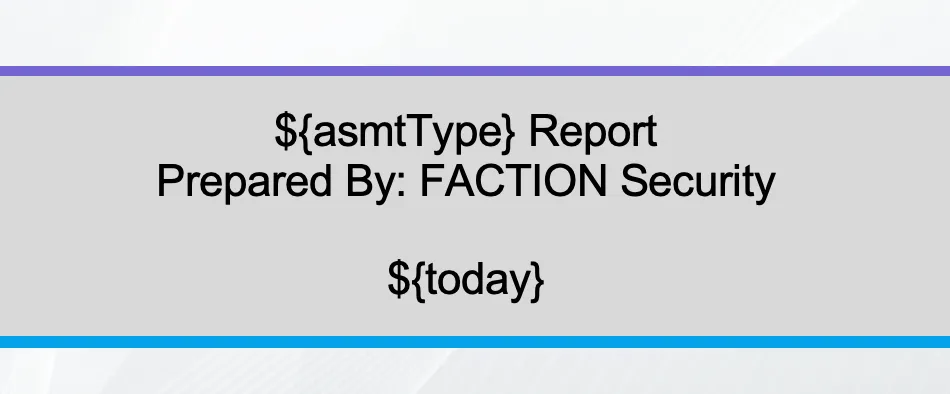 If you are just starting a pentest team and need to create a report from scratch, No Worries! Faction has several prebuilt templates you can start with. You only need to tweak your theme and move the elements around to your liking. This can get your new pentest consultancy up and running very quickly.
If you are just starting a pentest team and need to create a report from scratch, No Worries! Faction has several prebuilt templates you can start with. You only need to tweak your theme and move the elements around to your liking. This can get your new pentest consultancy up and running very quickly.
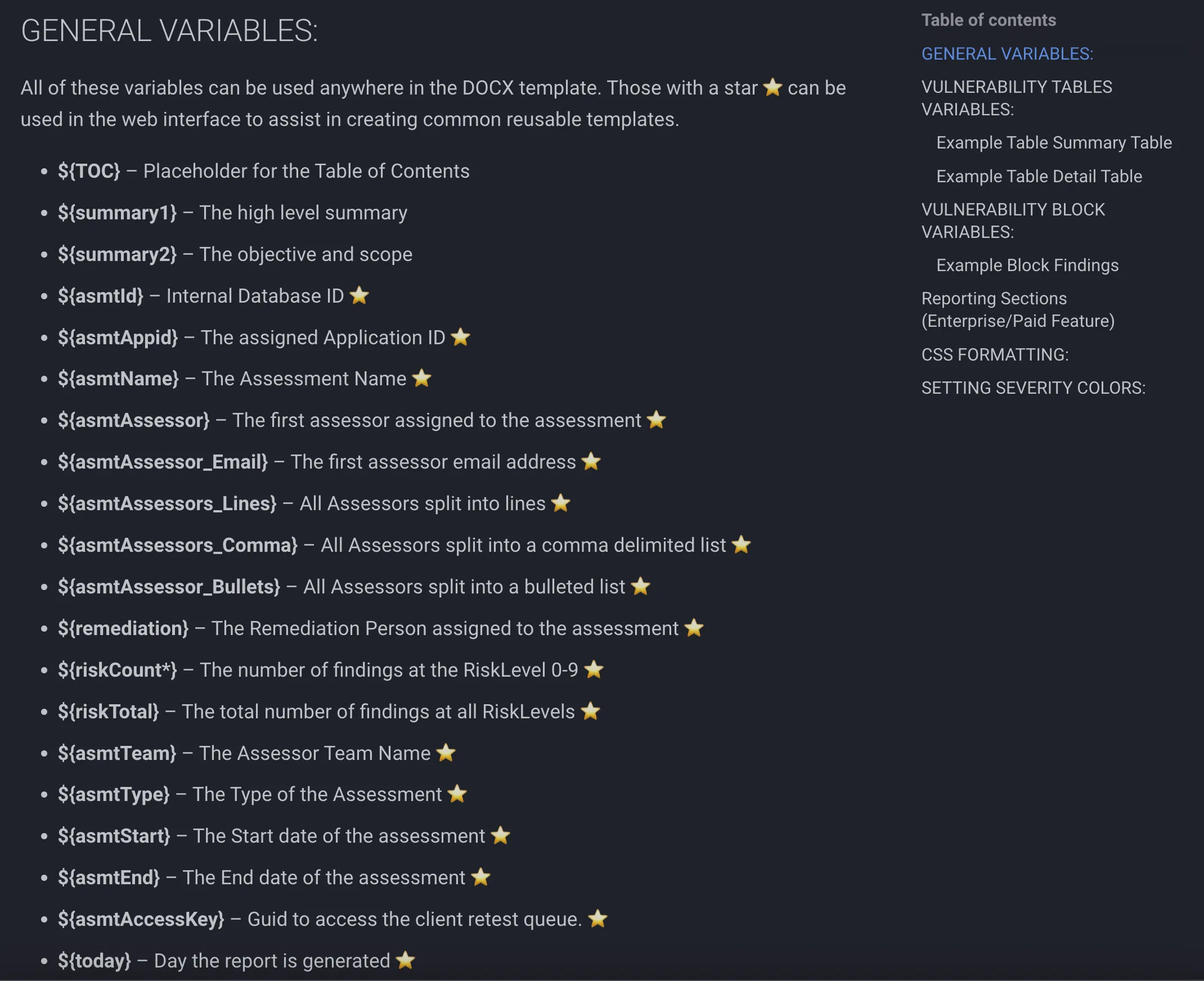
You can see all the variables that Faction supports here. If you need other items then you can use Faction’s Custom Variables and they will get auto-populated in the report as well.
Pentesting and Note-taking
Taking notes is an essential part of penetration testing. As you uncover issues, you’ll jot down details like URLs, parameters, and the steps to reproduce an attack. Many pen-testers rely on tools like Obsidian, OneNote, CherryTree, or similar apps to record this information. Whatever tool you choose, it needs to support rich text and make capturing screenshots quick and easy.
Typically, you’ll compile all your notes during the testing process, and at the end of the engagement, you’ll refine them into a professional report. This involves concisely documenting how to reproduce each finding, including boilerplate text to explain what the issue is, why it’s a risk, and common remediation steps. These details are critical for helping clients understand the business impact of the vulnerability while also showcasing your expertise in remediation. As ethical hackers, our mission goes beyond identifying risks — we provide actionable recommendations to strengthen the client’s security posture.
This is where Faction will save you a ton of time. Faction combines note-taking and reporting into one seamless app, eliminating the need to rewrite or reorganize your notes at the end of the assessment.
Faction allows you to customize common vulnerability boilerplates. For Example, you’ve probably found XSS thousands of times, and the description and recommendation details are mostly the same. So there is no need to write it over and over again. To add a finding in Faction, just search for the Vulnerability name (XSS for example), and Faction will populate the description and recommendation boilerplates for you as shown below:
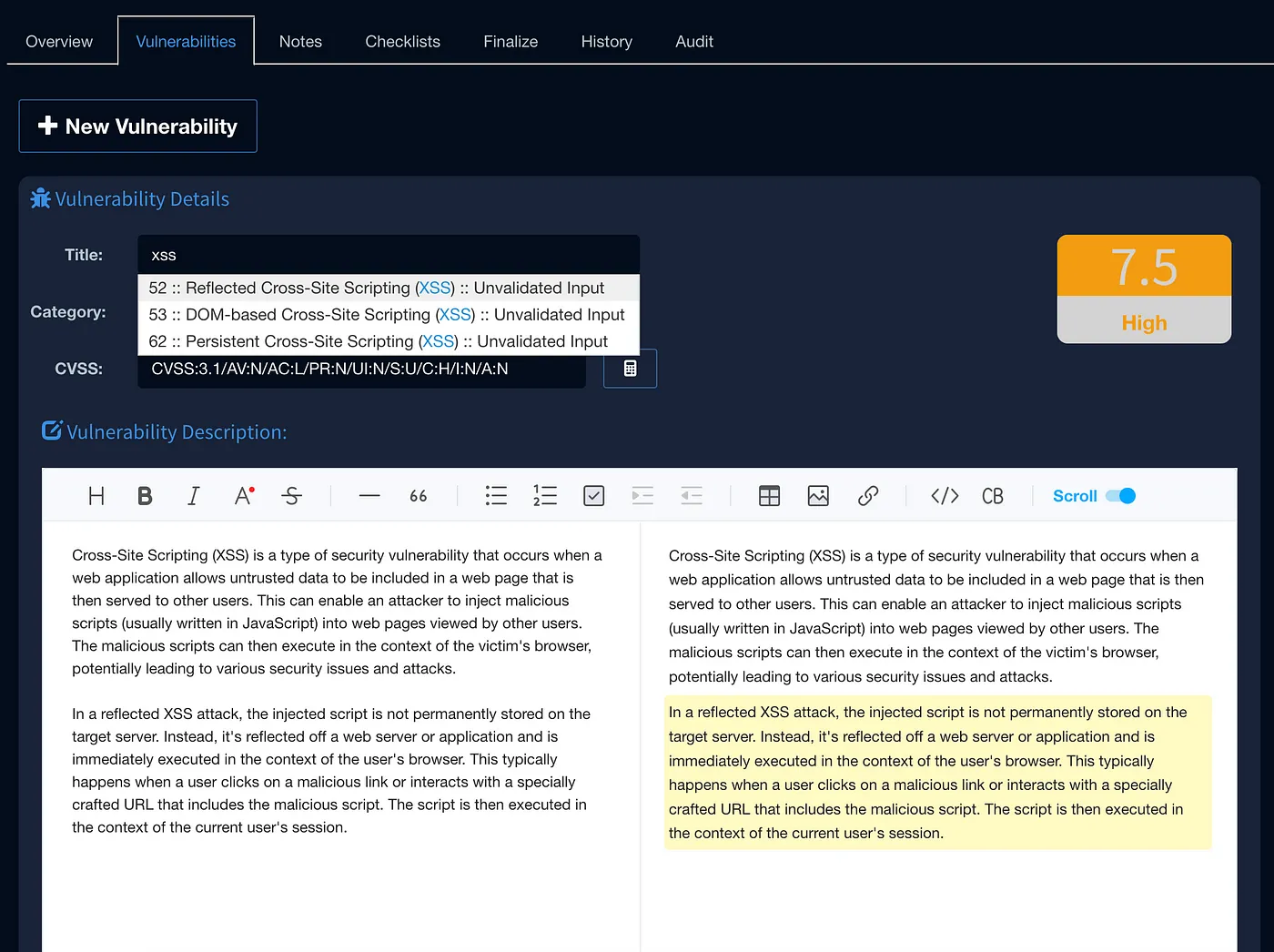
Now, you can enter your exploit steps using markdown and paste your screenshots directly into the text editor. Unlike using a standalone note-taking app, this approach integrates your findings into the report as you work. This eliminates the need to duplicate effort by reformatting or transferring notes at the end of the assessment, saving you time and ensuring consistency throughout the process.
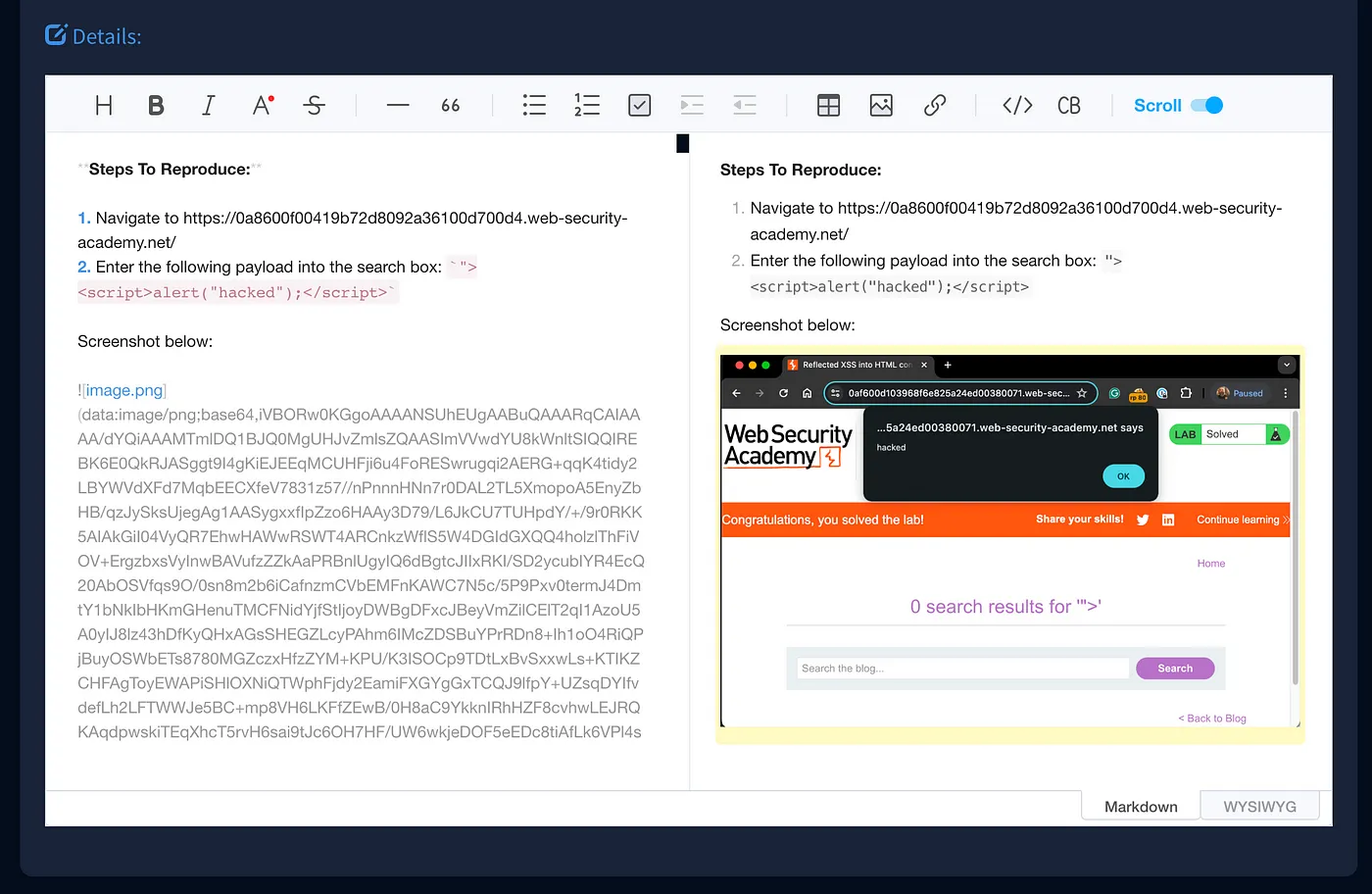
Faction also includes a collaborative notebook feature, enabling you to document and share noteworthy findings with your team in real time. This is perfect for capturing observations such as potentially insecure frameworks, partially successful attacks that require further exploration, reconnaissance data, and other insights gathered during the assessment.
Writing the Executive Summary
When writing a penetration test report, it’s essential to consider the audience who will be reading it. So far, we’ve focused on the Technical Findings section. This section, including Exploit Steps, is vital for technical teams, as they need detailed information to fully understand the issues and implement effective fixes.
The Executive Summary, on the other hand, serves a different purpose. It is tailored for managers and non-technical stakeholders, enabling them to evaluate the business risks, make informed prioritization decisions, and grasp the overall significance of the findings at a high level.
A strong Executive Summary addresses these concerns in clear, concise terms, avoiding technical jargon. It should provide a straightforward explanation of why the identified issues matter and offer guidance on prioritizing the findings outlined in the report.
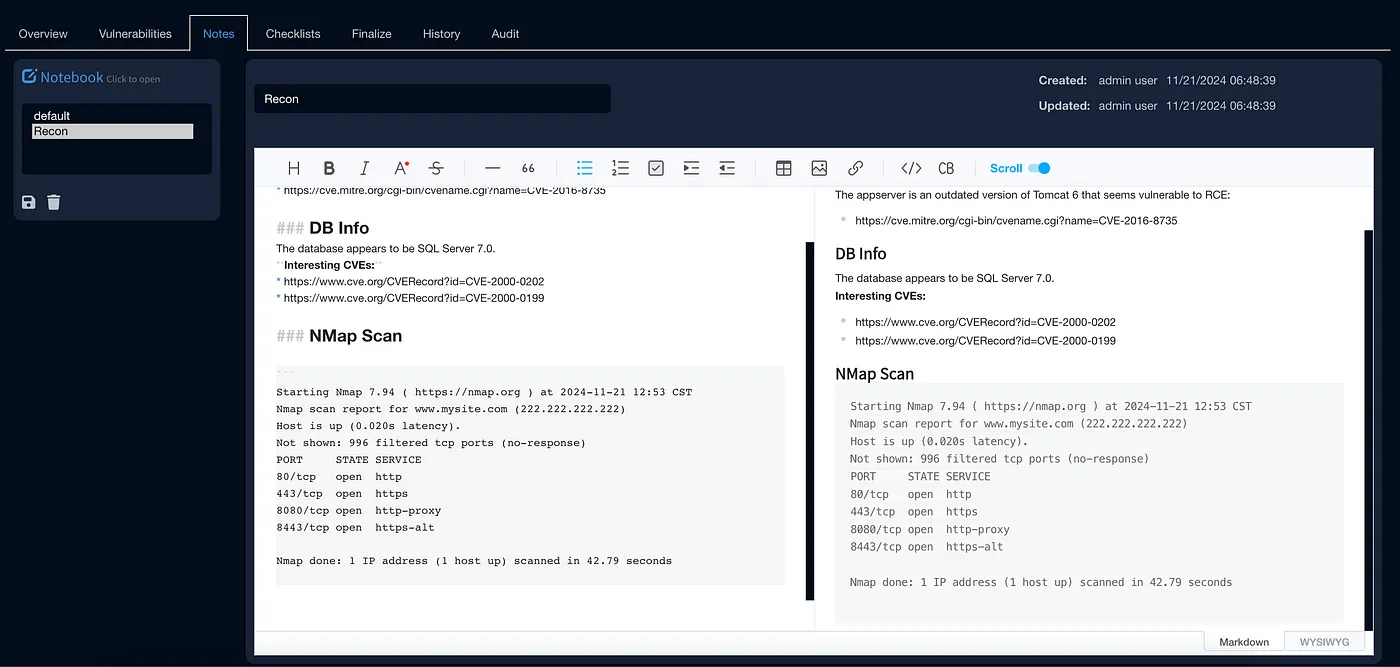
Certain sections of the high-level summary can often be standardized, requiring only minor adjustments for each specific assessment. To streamline this process, Faction offers global boilerplate templates that can be effortlessly incorporated into the Executive Summary. These templates can automatically populate variables, saving time and ensuring consistency.
In the screenshot below, you’ll see how easy it is — simply select the Executive Summary template from the menu on the right, and it instantly populates the text editor. The template includes customizable variables, such as severity and assessment type, to tailor the content to the current engagement. Best of all, these templates are fully customizable to align with the unique needs of your penetration testing program.
Peer Review the Report
Once all Technical Findings have been documented and the Executive Summary is finalized, the next step is to polish your assessment report. Faction’s Peer Review feature makes this process seamless by allowing your team to collaborate, suggest edits, and comment on each section of the report. This ensures the final deliverable is free of typos, accurately reflects risk calculations, and maintains a professional appearance.
When you submit a report for Peer Review, your team members are notified via the Peer Review Queue. This queue facilitates collaborative editing, enabling multiple reviewers to provide input and make adjustments. The process functions similarly to the Track Changes feature found in modern document editors, offering an intuitive way to finalize your report with precision and professionalism.
Finalize the Report and Track the Risk
Once the report has been peer-reviewed, it’s time to finalize it in Faction. Generate the final version of the report to share with the client and schedule your report-out meeting. This meeting is a critical step in the process, as it provides an opportunity to review all findings with the client, explain the associated risks to their business, and address any questions or concerns.
During this meeting, you’ll also discuss remediation SLAs — the timelines for addressing each finding based on its severity. For example, critical vulnerabilities might need to be remediated within 30 days, while high-severity issues could have a 60-day window.
Faction streamlines this by supporting custom SLAs for different risk categories. Tracking begins as soon as the report is finalized. You can configure settings to track only Critical and High findings while excluding Medium and Low findings if desired.
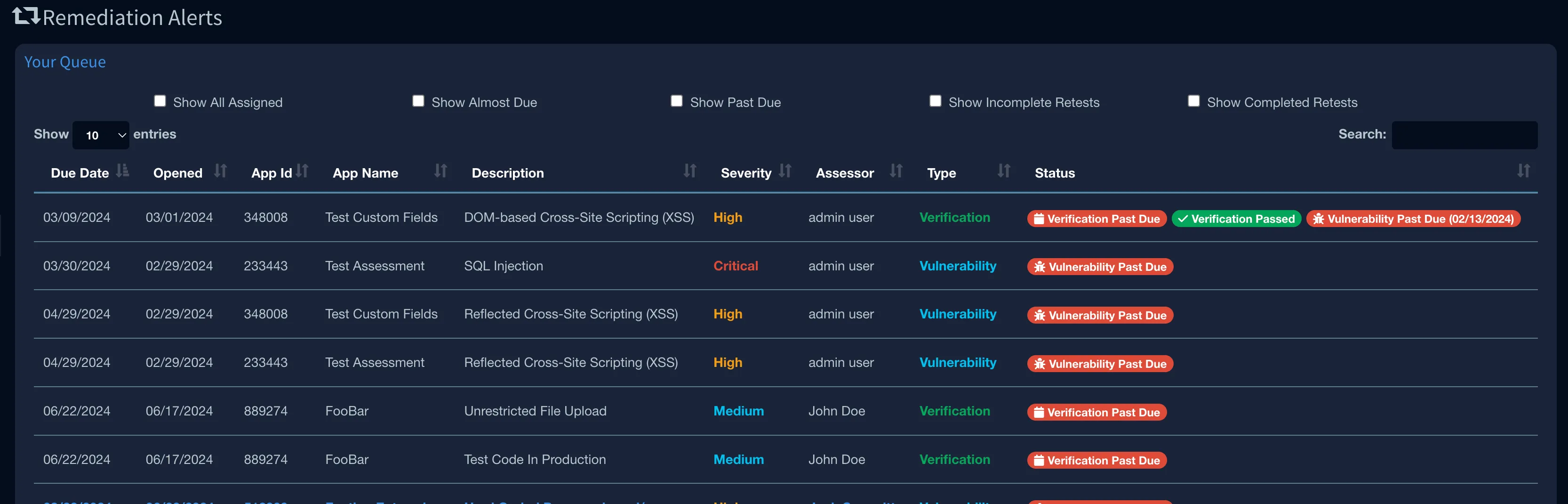
Faction’s Remediation Dashboard ensures you stay on top of the remediation process. It provides real-time insights into:
- Findings currently out for re-tests
- Issues approaching SLA due dates
- Findings that are past due
This proactive tracking ensures nothing falls through the cracks, helping both you and your clients maintain accountability and prioritize risk mitigation effectively.
Additional Information
Faction is free and open-source you can download it directly from GitHub here: https://github.com/factionsecurity/faction.
There is additional documentation on the main website: https://www.factionsecurity.com
